Resource Center
Insights, news, and updates from the leader in breach containment

Featured resources
%2520(1).webp)







6 Steps to Implementing a Zero Trust Model
Learn key best practices to building stronger Zero Trust security to protect against ransomware and other cyberattacks.








Illumio Insights in Action Guide
The incident response playbook for threat hunters, security operations teams, and forensic investigators
.webp)







The Illumio Breach Containment Platform
Detect, assess, and stop lateral movement across your hybrid environment with a single platform.








5 Questions to Ask Before Buying a Segmentation Solution
Learn the five critical questions to ask before buying a segmentation solution and avoid hidden risk with a Zero Trust architecture built to stop lateral movement.
.webp)







Illumio Segmentation for Cloud
Contain cloud breaches faster with Illumio Segmentation for Cloud, delivering real-time visibility and Zero Trust enforcement to stop lateral movement across workloads.








2026 Gartner® Peer Insights™ Voice of the Customer for Network Security Microsegmentation
Learn why Gartner named Illumio a Customers' Choice for network security microsegmentation.
.webp)







The Breach Containment Buyer's Guide
Understand how to separate containment claims from reality and what it takes to stop lateral movement before damage spreads.








Simplifying Segmentation: How Microsegmentation Powers Zero Trust and Breach Containment
Discover how microsegmentation strengthens Zero Trust by stopping lateral movement and containing breaches faster and more effectively.








Compliance, Breach Containment, and Cyber Resilience for the Banking Sector
Learn how Illumio addresses cyber risk in banking — meeting regulatory pressure, overcoming CISO challenges, and delivering breach containment, Zero Trust segmentation, and operational resilience across hybrid environments.
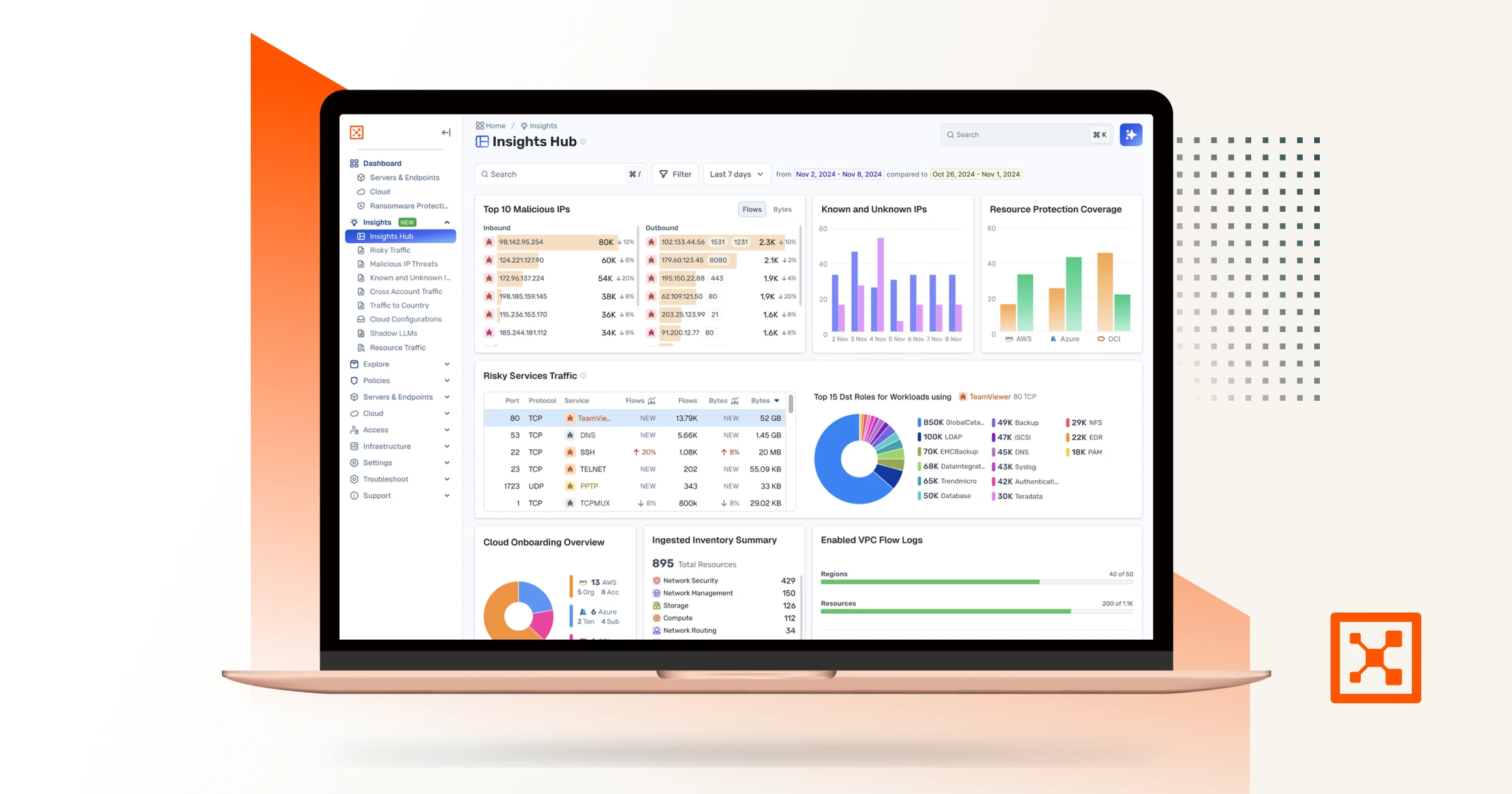







Illumio Insights
Learn about hybrid multi-cloud detection and responsesolution built on an AI-powered security graph
.webp)







Advancing Segmentation to Strengthen Security and Compliance in Financial Services
Strengthen cyber resilience in financial services with Illumio + IBM by using segmentation and expert guidance to meet DORA, SWIFT, PCI-DSS, and global compliance needs.
.webp)







Illumio and IBM: Securing Quantum Computing with Illumio Segmentation
Prepare for post-quantum threats with Illumio and IBM by combining segmentation and quantum-safe cryptography to stop lateral movement and ensure long-term resilience.








The Buyer’s Guide to Detection and Response
Learn how to evaluate core detection and response technologies for today’s (and tomorrow’s) threat landscape.


